[ad_1]
Store Crypto safely with wallets
While the above steps can help protect you from an exchange attack, ultimately you are not in control as long as the exchange has your crypto. This is where crypto wallets come in.
What is a Crypto Wallet?
A crypto wallet is like a literal wallet where you can store your cryptocurrencies, only since cryptocurrencies are digital, crypto wallets are also virtual. It is a piece of software that you can use to prove that you are the owner of a particular crypto account or address. You can use a wallet to securely store cryptocurrency or to authorize crypto payments to employees or merchants.
Unlike exchanges, wallets live on your device, so the only way for an attacker to get crypto from your personal wallet is to attack your personal device. While it’s always possible that your device could be hacked, it will generally be less attractive to a target than your exchange. So the most effective strategy you can use to protect your crypto is to move it to a private wallet.
>> Also Check: Is Crypto.com Safe?
Cryptography and how it appears in crypto wallets
Cryptography plays a major role in cryptocurrency. Wallets use cryptography to verify transactions. When you create a wallet, it generates a hash of your “address”, which uniquely identifies your wallet. For example, to send someone crypto, you would ask for their hashed address, and if someone wanted to send you crypto, you would give them your address.
The hash transmitted during transactions contains important information – for example, the amount transferred and the recipient’s address, signed with the sender’s private key – in code (encrypted). To interpret the code, validators will need to use a public key generated by the sender’s wallet, and for the transaction to push through, all the pieces of information must match.
This is an oversimplification of the process. There is much more going on in the background, but the bottom line is clear: Cryptography in wallets and the blockchain play a major role in crypto-security.
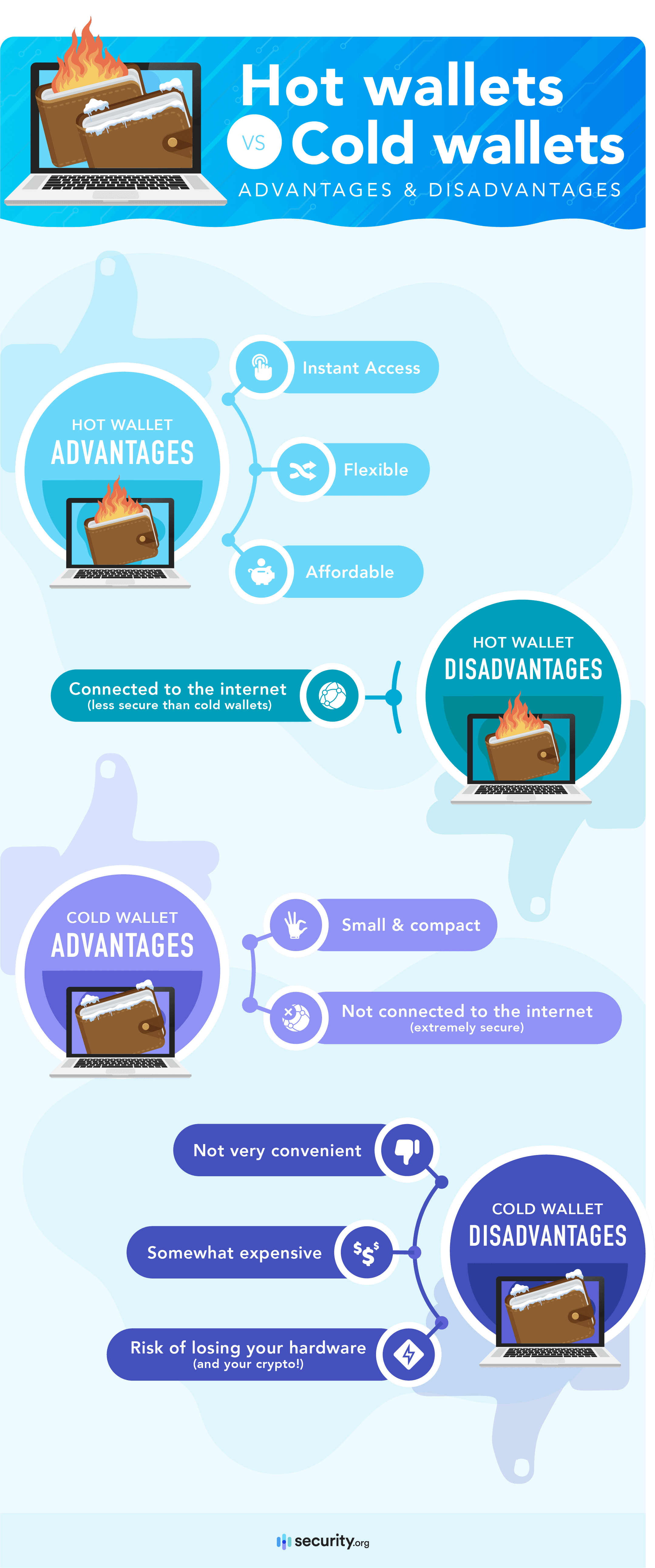
Hot wallets vs cold wallets
Now, about the different types of crypto wallets, there are two that you absolutely need to know about before you get started: Hot wallets and cold wallets.
A hot wallet is a piece of software that runs on a device connected to the Internet, such as a computer or mobile wallet. You can download hot wallets from websites or from mobile app stores.
A “cold wallet”, on the other hand, is a wallet that is not connected to the internet. These include paper wallets and hardware wallets. Cold wallets cannot be downloaded; they can only be bought or created.
If you’re going to use your crypto on a daily basis, you might want to keep it in a warm wallet. But if you’re just buying and holding, a cold wallet is the safer option.
Use a hot wallet to store crypto
To store your crypto in a hot wallet, first download it from the official website and run the setup file.
Setting up the application (seed words, passwords and addresses)
When the app opens, it will display a set of seed words. These seed words are used to generate your crypto accounts and addresses.
Write these words down on a physical piece of paper in the order they are given to you. Do not take a screenshot of these words or save them to any kind of cloud service such as Dropbox or Google Drive.
Store your physical backup in a safe place where it cannot get wet, catch fire, or otherwise be destroyed. Don’t tell anyone where it is unless you intend for them to have access to your crypto.
Passwords
After allowing you to record your seed words, the app will ask you for a password. Use a strong password with numbers, upper and lower case letters, and special characters if possible.
If you forget your password, you can recover your account with your seed words. So don’t stress about forgetting it. But make sure you don’t lose your physical copy of your seed words.
Addresses
When you have completed this process, you will see your cryptocurrency address. This is a long string of characters derived from your seed words.
When you withdraw your crypto, your exchange will ask for this string of characters. Make sure to copy and paste the address instead of typing it by hand. If you omit or change just one character, you will lose the crypto you send!
Once your crypto is securely transferred to your wallet, the exchange will no longer have control over it. At this point, even if an attacker gets access to your exchange account, they won’t be able to steal your crypto.
Understanding hot wallet security
Now that your crypto is in your hot wallet, you need to make sure it is protect against attacks.
The seed words you copied onto the piece of paper are used to generate an unlimited number of private keys. A private key is a string of characters that your device uses to sign transactions and to prove that you are the owner of the account.
Each private key corresponds to an account or address. You can create as many addresses as you want from a single set of seed words.
Your seed words are stored on your device in a file called a key vault. This file is encrypted with your password. When you transact or browse crypto-enabled websites, your wallet will ask for your password to decrypt this file.
For an attacker to get your crypto, they need to steal both your key vault and your password. If they only have one of these items, they can’t get your crypto. They need both.
There is a hash of your password on your device. If your password is weak and the attacker gets this hash, they might be able to crack it by guessing millions of random strings of characters until they find one that produces this hash. This is why it is important to use a strong password.
List of secure hot wallets
Here is a chart showing some of the safest hot wallets. In each case, we have provided a link to the official website where an authentic copy of the software can be downloaded. We’ve also listed the type of wallet (computer or mobile) and the networks it can be used on.
Software Crypto Wallets
Wallet Type Networks Official Website Electrum Desktop Bitcoin Electrum.org Mycelium Mobile Bitcoin Mycelium.com Exodus Desktop and mobile Multiple Exodus.com Metamask Desktop and mobile Ethereum, BSC, Avalanche, HarmonyONE Metamask.io Brave Browser Desktop and mobile Ethereum, BSC, Avalanche, HarmonyONE Brave.com Coinbase Wallet Desktop and Mobile Ethereum, BSC, Avalanche, HarmonyONE Coinbase.com/wallet
Use a cold wallet to store crypto
Hot wallets can be extremely secure if you use them correctly, but they can still be compromised if your device becomes infected with keystroke logging software. This is where using a cold wallet can help protect you further.
If used correctly, a cold wallet should be impossible to hack except through physical theft.
Hardware wallets
The most popular form of a cold wallet is a hardware wallet. A hardware wallet is a small USB device that stores a keystore file. If you want to make a transaction with a hardware wallet, you can connect it to your computer or mobile device and send a signature through the USB port.
However, the key vault is stored on a separate memory bank in the device and cannot be transmitted in an unencrypted form via USB. This means that even if an attacker infects your computer with malware, they won’t be able to access your crypto.
The biggest risk of using a hardware wallet is physical theft. To protect even further against this possibility, hardware wallets have PIN code locks.
Security experts were able to hack hardware wallets using very sophisticated techniques once they had physical possession of them. So if you lose your hardware wallet, it’s best to transfer your crypto from the wallet as soon as you notice it’s missing.
The biggest drawbacks to hardware wallets are inconvenience and cost.
If you use a hardware wallet, you must connect the wallet to your computer and confirm the transaction with both the USB device and the software running on your computer. This can be quite inconvenient if you make a lot of transactions.
Additionally, hardware wallets typically cost $49-$220. So they are not economical to store very small amounts of crypto.
List of hardware wallets
Here is a list of some of the more popular hardware wallets. We have also included key features and pricing for these.
Hardware Crypto Wallets
Model Features Price Trezor Model T Supports all major networks; large, full-color touchscreen (no buttons) $185-$220 Ledger Nano X Supports all major networks; Bluetooth for mobile devices, large buttons, black and white OLCD display $119-$149 Ledger Nano S Supports 27 different networks; small buttons, black and white OLCD display $59 Keepkey Supports 7 different networks; small buttons, large OLCD screen $49
Paper wallets
Another form of cold wallet is a paper wallet. A paper wallet is a private key and address stored only on a piece of paper. Since the key is not stored on any kind of computing device, it should be impossible for a hacker to steal it.
In the early days of Bitcoin, paper wallets were very popular as a method of storage.
But unfortunately, this method turned out to have one major security flaw: to generate the key and address, you had to download an application in your browser. And it was hard to know if the app was sending your keys to the web server and exposing your account.
Today, paper wallets should not be considered safe.
Now that we’ve got the basics of wallets out of the way, let’s discuss some common crypto scams to watch out for.
[ad_2]
Disclaimer for Uncirculars, with a Touch of Personality:
While we love diving into the exciting world of crypto here at Uncirculars, remember that this post, and all our content, is purely for your information and exploration. Think of it as your crypto compass, pointing you in the right direction to do your own research and make informed decisions.
No legal, tax, investment, or financial advice should be inferred from these pixels. We’re not fortune tellers or stockbrokers, just passionate crypto enthusiasts sharing our knowledge.
And just like that rollercoaster ride in your favorite DeFi protocol, past performance isn’t a guarantee of future thrills. The value of crypto assets can be as unpredictable as a moon landing, so buckle up and do your due diligence before taking the plunge.
Ultimately, any crypto adventure you embark on is yours alone. We’re just happy to be your crypto companion, cheering you on from the sidelines (and maybe sharing some snacks along the way). So research, explore, and remember, with a little knowledge and a lot of curiosity, you can navigate the crypto cosmos like a pro!
UnCirculars – Cutting through the noise, delivering unbiased crypto news







