[ad_1]
Quantum computing won’t just challenge modern cryptography—it could forever change how we approach data encryption.
Much of the discourse surrounding quantum computing concerns the opportunities it offers in areas such as electric cars, supply chain optimization and chemical research. But people are concerned about the impact quantum computing will have on cryptography and whether modern encryption methods will still be sufficient to protect data. Although this threat is years away, data center managers and security teams must be familiar with it and work together to adapt for the future.
Quantum computers could theoretically break many of the encryption methods organizations use today as quantum computers undergo more research and development. Quantum attacks can pose a risk to asymmetric and symmetric cryptography encryption methods because quantum computers may be able to perform calculations that can decrypt them. However, many researchers are exploring options for encryption methods that can protect data center infrastructure from quantum attacks.
Quantum computing can affect the effectiveness of encryption
Much of today’s modern cryptography is based on mathematical algorithms used to encrypt data. With quantum computers, attacks on encryption methods that normally take years can theoretically be done in days with quantum computers. Asymmetric and symmetric encryption types can both be at risk. Many organizations often use encryption types that fall into these categories in a variety of data center assets, including storage and networking devices, in addition to areas such as secure email and web browsing.
Shor’s algorithm poses threats to asymmetric cryptography
Rivest-Shamir-Adleman (RSA) encryption and most public-key cryptography — also known as asymmetric cryptography — are built on the ability to use mathematical algorithms to encrypt data. For example, RSA uses integer factorization with two prime numbers. A public and private key are generated that are mathematically related in public key algorithms, according to IBM. Even with a brute-force attack, it can take years for a classic computer to break encryption methods like RSA.
The security of RSA and other asymmetric algorithms depends on the difficulty of factoring large numbers. Factoring large numbers is the strength of Shor’s algorithm. Many public-key cryptographies use prime factorization to generate keys, but Shor’s algorithm could in theory break asymmetric cryptography with quantum computers, given their ability to perform complex calculations quickly. Quantum computers can perform decryption without knowing the private key, according to the Technology and Privacy Unit of the European Data Protection Supervisor.
Shor’s algorithm can also compromise other encryption schemes, including Diffie-Hellman and elliptic curve cryptography (ECC), using quantum computers.
Grover’s algorithm goes to symmetric cryptography
Organizations can also use symmetric cryptography, or secret key cryptography, to encrypt stored data. Examples of symmetric encryption algorithms are Advanced Encryption Standard (AES), Rivest Cipher 4 and Triple Data Encryption Algorithm.

Symmetric encryption converts plaintext into ciphertext and uses a single key for encryption and decryption of data. For example, AES-256 requires a 256-bit key to encrypt and decrypt data. A brute-force attacker would need to guess the key out of about 1.1579209 x 1077 possible keys, or 2256 keys, according to IT management and service provider N-able. This makes AES-256 and other similar symmetric encryption algorithms secure.
However, someone sophisticated enough to run Grover’s algorithm with quantum computing power can use it to find encryption keys. Grover’s algorithm enables someone to search large databases much faster than a classical computer. If an algorithm has N, a number of items, Grover’s algorithm can search through the list of items and find a specific one in √N steps, according to IBM. This reduces the time it takes to find the key.
Bad actors can also use Grover’s algorithm to break hash functions, such as Secure Hash Algorithm 2 and 3, using a quantum computer.
Candidates for post-quantum cryptography and quantum-resistant encryption
There are several options being researched to help hedge against the threat of quantum computing-based attacks on data center infrastructure and data. Many are based on cryptography that some researchers and experts believe can be quantum-proof.
Lattice-based cryptography
Lattice cryptography is based on the mathematical concept of lattices and vectors. Most current cryptography follows algebraic problems, but lattice-based cryptography is based on geometry. Lattice-based computational problems are based on the shortest vector problem, where an attacker must find a point closest to the origin. But when introducing multiple dimensions, as opposed to a two-dimensional grid, it’s incredibly difficult to solve that problem. Some believe that early quantum computers may not be able to break grid-based encryption, and this is the most promising option.
Quantum key distribution
Quantum key distribution (QKD) uses quantum mechanics to distribute keys. It relies on the fact that, if you measure a quantum system, it will be perturbed. Therefore, if a malicious actor tries to intercept the key, the parties will know about eavesdropping.
Photons are transmitted between parties over fiber optic cables, where each photon has a random quantum state. When a photon is transmitted and reaches its destination, it passes through a beam splitter and chooses some path at random in a photon collector. Since the receiving party does not know the correct polarization, it then measures the polarization of the photons and shares that information with the sender over another channel. The photons read with the wrong splitter are ignored, and the remaining sequence is used as the key.
QKD is still evolving. However, the National Security Agency said this is only a partial solution to quantum security.
Code-based cryptography
Code cryptography is based on error correcting codes. This is based on how difficult it is to decode messages containing random errors where the attacker has to recover the code structure. One of the most famous is the classic McEliece algorithm.
NIST asked cryptographers to start researching quantum-resistant encryption algorithms for its review and considered McEliece. However, NIST has not standardized it due to its large public key sizes, but it is undergoing further review.
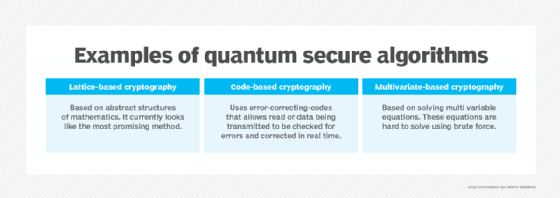
Multivariate-based cryptography
Multivariate cryptography is based on the difficulty of solving systems of equations. It uses a randomized system of polynomial equations where the receiver must use a private key to perform inverse operations on the generated ciphertext. Even with the encrypted data, attackers would have to solve the equations to read it, which is a computationally difficult task.
Isogeny-based cryptography
Isogeny-based cryptography is similar to ECC in that it uses elliptic curves to encrypt data. Instead of relying on the logarithmic problems that an ECC method would, isogeny-based cryptography relies on isogenies, or maps between elliptic curves. Like grid-based cryptography, these calculations could be difficult enough that they would be quantum-resistant.
Other areas organizations are exploring for quantum-resistant encryption include zero-knowledge proofs and hash-based cryptographic systems.
How we prepare for post-quantum cryptography
In 2016, NIST asked cryptographers to start researching and developing quantum-resistant encryption methods and submit them for review. In 2022, NIST selected four potential quantum-resistant cryptographic algorithms to become part of its post-quantum cryptographic standards, and more are under review.
Three of the algorithms are based on structured grids, and one uses hash functions, according to NIST. In the fourth round of consideration, NIST will examine four more algorithms. Three are code-based, while the remaining are isogeny-based. Some will be used for general encryption, and others will be used for digital signatures.
Although the consensus is that a serious security threat from quantum computing is many years away, data center administrators and security teams should not wait to prepare. Quantum computer security threats probably won’t be a problem — until they are. In an interview with TechTarget Editorial, security expert Tim Hollebeek said people should look at where they use cryptography in their systems, “what it protects and what are the data protection lifetimes associated with that data.”
Start working with security teams and stakeholders to prepare systems for a post-quantum world, and plan hardware and software upgrades where necessary. Stay tuned with NIST as it reviews post-quantum algorithms and assesses potential options for quantum-resistant encryption.
[ad_2]
Disclaimer for Uncirculars, with a Touch of Personality:
While we love diving into the exciting world of crypto here at Uncirculars, remember that this post, and all our content, is purely for your information and exploration. Think of it as your crypto compass, pointing you in the right direction to do your own research and make informed decisions.
No legal, tax, investment, or financial advice should be inferred from these pixels. We’re not fortune tellers or stockbrokers, just passionate crypto enthusiasts sharing our knowledge.
And just like that rollercoaster ride in your favorite DeFi protocol, past performance isn’t a guarantee of future thrills. The value of crypto assets can be as unpredictable as a moon landing, so buckle up and do your due diligence before taking the plunge.
Ultimately, any crypto adventure you embark on is yours alone. We’re just happy to be your crypto companion, cheering you on from the sidelines (and maybe sharing some snacks along the way). So research, explore, and remember, with a little knowledge and a lot of curiosity, you can navigate the crypto cosmos like a pro!
UnCirculars – Cutting through the noise, delivering unbiased crypto news







